Technologies that facilitate employee monitoring
There are no end of solutions on the market that contain a vast array of technologies to facilitate employee monitoring. From time tracking software that monitors task durations to sophisticated AI that analyses behavioural patterns, these technologies are diverse.
TRACKING USERSEMPLOYEE MONITORING
Tim Clements
6/20/20244 min read
There are no end of solutions on the market that contain a vast array of technologies to facilitate employee monitoring. From time tracking software that monitors task durations to sophisticated AI that analyses behavioural patterns, these technologies are diverse. For example, keyloggers track every keystroke, providing insights into user behaviour. Network monitoring oversees network traffic to secure data and prevent unauthorised access, yet they must be managed carefully to avoid overreach.
Often integrated into sophisticated packages the technologies automate employee monitoring practices that have been around for over a hundred years. See this blog post to get an understanding of the history and origins of employee monitoring.
Understanding these tools' capabilities and risks is crucial for their ethical and legal application. To help guide you, we've produced this infographic that summarises some of the key technologies available but there are many more available and are evolving at a rapid pace.
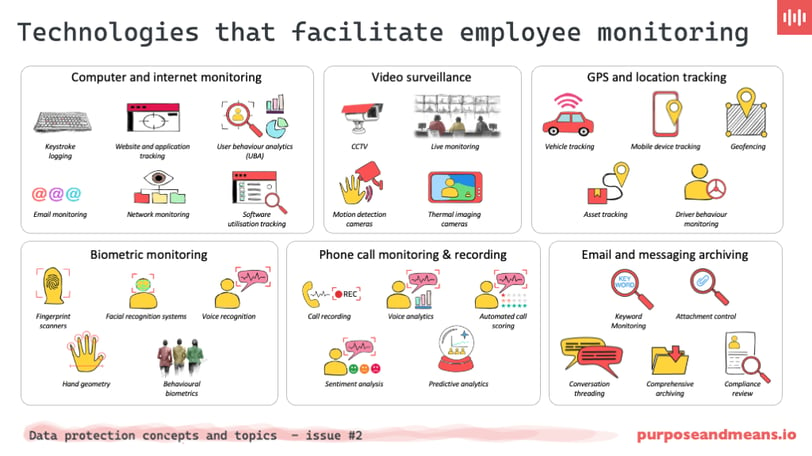
Computer and internet monitoring
Keystroke logging: captures every keystroke made on a computer, allowing employers to see what employees type, which can include emails, documents, and chat messages.
Website and application tracking: monitors which websites and applications employees access during work hours to ensure they are using company resources appropriately.
User Behaviour Analytics (UBA): utilises advanced algorithms to assess patterns of user activity on company networks to identify anomalies that could indicate insider threats or security risks.
Email monitoring: involves scanning and analysing inbound and outbound emails for content compliance, security risks, and productivity assessment.
Network monitoring: observes data flow over a company’s network to detect unauthorised access, data breaches, and to ensure network security and efficiency.
Software utilisation tracking: measures how employees use software applications to manage licensing compliance and to optimise software investments based on actual usage.
Video surveillance
CCTV: Closed-Circuit Television (CCTV) is a type of video surveillance system that uses cameras to monitor and record activities in specific areas for security and monitoring purposes.
Live monitoring: real-time observation using video cameras to ensure workplace safety, security, and compliance with company policies.
Motion detection cameras: cameras that start recording only when motion is detected, helping to save storage space and focus monitoring on periods of activity.
Thermal imaging cameras: used to detect heat patterns, which can be used in specific industrial settings for safety and also to track human movement.
GPS and location tracking
Vehicle tracking: utilises GPS devices installed in company vehicles to monitor their locations and movements to optimise fleet management.
Mobile device tracking: tracks the location of company-provided mobile devices to ensure that employees are at their assigned locations during work hours.
Geofencing: sets up virtual boundaries that trigger alerts when an employee enters or leaves a specific geographical location, used for ensuring compliance with operational constraints.
Asset tracking: utilises technologies like GPS and RFID chips to monitor and manage the location and status of valuable assets, such as equipment or merchandise, in real-time to enhance security and operational efficiency.
Driver behaviour monitoring: employs GPS and other sensor technologies to analyse driving patterns, such as speed, braking, and cornering, to ensure safe driving practices and optimise fleet performance.
Biometric monitoring
Fingerprint scanners: commonly used at entry points or on time clocks to verify an employee’s identity based on their unique fingerprint.
Facial recognition systems: used for security access and timekeeping by analysing facial features to confirm an individual's identity.
Voice recognition: utilises voice patterns to authenticate identity, often used in secure communication systems.
Hand geometry: measures the shape and size of an employee’s hand for access control, typically in high-security areas.
Behavioural biometrics: analyses behavioural patterns like typing rhythm, mouse movements, and walking patterns for continuous verification of authenticated users.
Phone call monitoring & recording
Call recording: records calls to or from company phones, often used in customer service and sales environments to monitor quality and compliance.
Voice analytics: uses advanced algorithms to analyse spoken content for tone, stress, and emotional sentiment to improve customer interactions and employee training.
Automated call scoring: uses pre-defined criteria to automatically evaluate the quality of calls handled by employees, aiding in performance reviews and training.
Sentiment analysis: applies natural language processing tools to detect emotional tones in voice communications, which can inform customer service strategies.
Predictive analytics: uses data from recorded phone calls to forecast trends and patterns in employee performance, customer satisfaction, and operational efficiency, helping managers make informed decisions and improve future interactions.
Email and messaging archiving
Keyword monitoring: scans emails and messages for specific keywords that may indicate compliance issues, security threats, or other concerns.
Attachment control: monitors and regulates files attached to emails to prevent the spread of malware and the leakage of sensitive information.
Voice analytics: uses advanced software to analyse tone, stress levels, and spoken content to gauge performance and compliance.
Conversation threading: organises emails and messages into threads, making it easier to review the full context of conversations for audits and compliance checks.
Comprehensive archiving: this involves the systematic storage of electronic records, such as emails, chat messages, and documents, to ensure that all communications are retained securely over time. In employee monitoring, comprehensive archiving helps organisations maintain detailed records of employee communications for various purposes including historical reference, performance review, and legal compliance. It ensures that data is accessible for audits or investigations, providing a reliable resource for understanding past activities.
Compliance review: this refers to the regular examination of stored communications and other monitored data to ensure that the organisation's activities are in line with legal standards, industry regulations, and internal policies. Compliance reviews are critical in employee monitoring as they help organisations verify that the monitoring practices themselves, as well as employee actions, adhere to relevant laws and regulations (such as GDPR or HIPAA). These reviews aid in identifying and mitigating risks associated with non-compliance, which can include legal penalties and reputational damage.
Do you find these infographics useful? We research and produce one-pagers, explainers and similar infographics for a wide range of topics, and have found they are a popular addition to our clients' employee engagement activities, supporting the education and training programmes we provide.
Interested? Book a discovery call to hear more about how Purpose and Means can support your own employee engagement activities, putting original, contextual and highly visual material in front of your company's employees.
Purpose and Means
Helping compliance leaders turn digital complexity into clear, actionable strategies
BaseD in Copenhagen, OPerating Globally
tc@purposeandmeans.io
+45 6113 6106
© 2025. All rights reserved.
